A while ago I was asked in comments about my OpenWRT IPv6 setup. So I decided to write a small note about it here in my blog. Sorry for missing some of the theory and the details – it’s meant for those who are in a hurry.
We all know that IPv4 addresses are running the hell out, IPv6 *SHOULD* be already used extensively, but many of our local providers just don’t bother themselves with it. And since in terms of setup IPv6 is way more complicated to properly set up compared to IPv4 a lot of sysadmins don’t bother themselves setting it up just because – ‘IPv4 will be ‘nough for our age, man’. As for me, I decided to set up some basic IPv6 in my LAN just to test things out, have an ability to test my own apps over IPv6, and, well, be prepared for the future, you know.
My server is running on a shelf at home, behind an OpenWRT router. I get my IPv4 address at the WAN interface with DHCP. Thankfully the age of PPTP/PPPoE is over at last (as is the age lanparties. I really miss ’em).
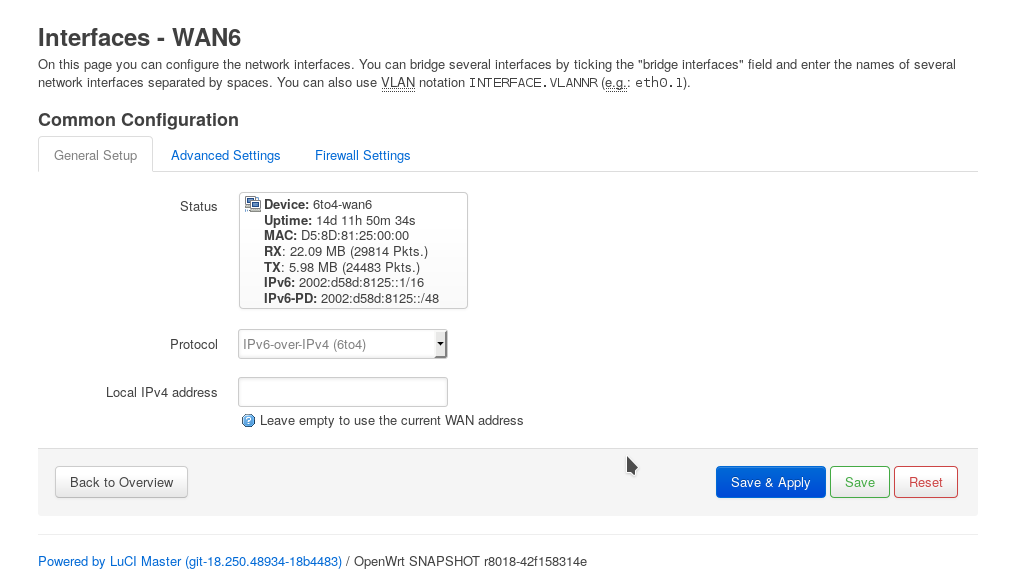
Since I didn’t have much time for setup I decided to do things as simple as possible. Waiting for my provider to offer IPv6 was not an option – I’d retire earlier, so I decided to use one of the transition mechanisms available. So, to make things short and simple, it’s either a miredo/teredo tunnel, or a thing called 6-to-4, that is pretty good, since the IPv6 range you’ll get is as static as your IPv4 address. Besides, you don’t need to find a tunnel broker – it will find one on its own (though you can’t choose which one, though), so it’s even easier.
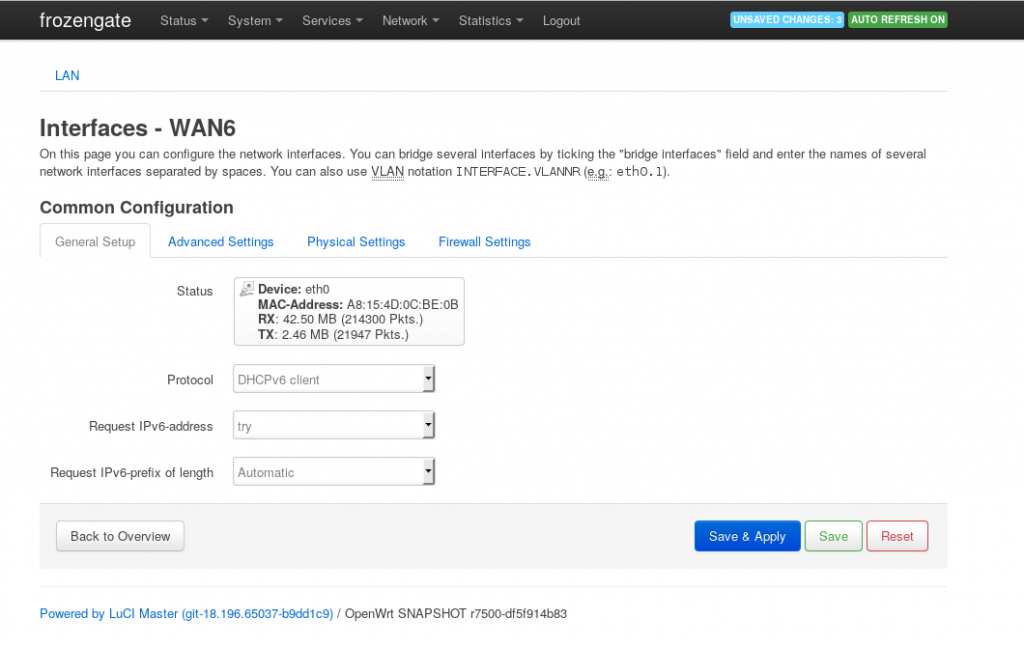
In LUCI, once we’ve just flashed OpenWRT you normally have WAN, LAN interfaces, and a WAN6 interface. The setup looks like this:
This is the thing we’re going to tune. In my case it looked like this:
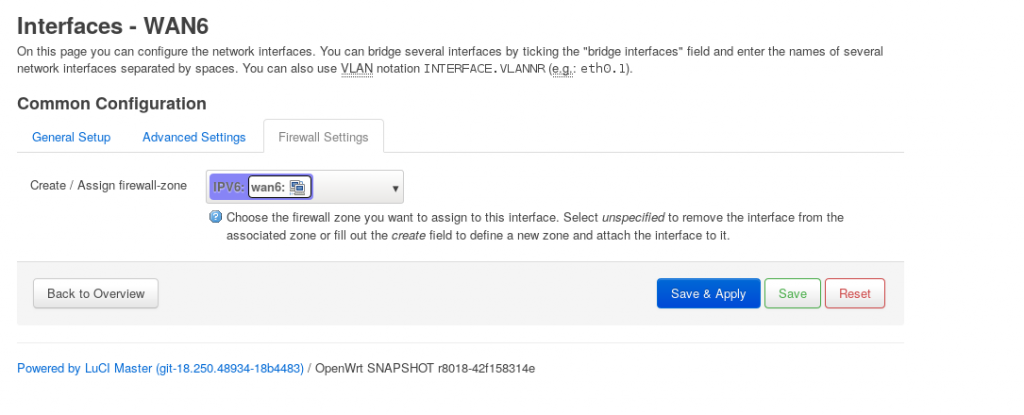
If you haven’t really touched DHCP and LAN settings with any super-complex setups, everything should “just work” and all you LAN clients will get their shiny IPv6 addreses once configure 6to4. But we’ll run into a huge problem here: Everything on the network that is IPv6-capable will be directly exposed to the Internet which is NOT a wise idea even if you’re running only linux. To fix this, we’ll add WAN6 to a new firewall zone:
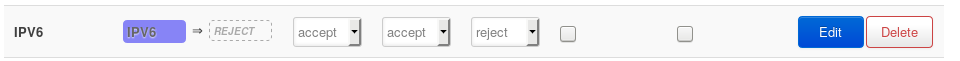
And configure the zone in this way:
To test the setup you’ll need either a VPS with IPV6 enabled or use online tools like this one. Once done with the firewall, IPv6 address of the router will be directly accessible from outside, but none of the computers on our internal network. On the other hand, all computers inside our network will be able to use IPv6 sites with no problems. Well, that covers it. Looks simple enough.
This setup is very IPv4-like, and all the usual port-forwarding stuff stays the same for both IPv4 and IPv6, so you’ll have less to set up when you need to use port from the outside. In my case all http traffic goes through the router anyway, where it’s reverse-proxied via nginx.
Email server on the other hand is a totally different story. For it to work you have to get a reverse PTR entry in DNS. For IPv4 that was done by my ISP. This will not work with this IPv6 setup, and according to the manuals on the Internet you’ll have to install BIND (and have a dance setting it all up) for this to work. So for now I’ve disabled IPv6 in my email server for now.
P.S. For brutal folks with red eyes that need “no freakin’ graphical user interface”, and prefer to write dangerous spells in configuration files by hand only, here are the relevant spells and places where you need to put them:
/etc/config/network
config interface 'wan6'
option proto '6to4'
/etc/config/firewall:
config zone
option name 'IPV6'
option input 'ACCEPT'
option forward 'REJECT'
option output 'ACCEPT'
option network 'wan6'
config forwarding
option dest 'IPV6'
option src 'lan'
Thanks, but editing a text file isn’t brutal. It’s child play 😉
If you are cognisant of what you are up to.